Mobile device management: Difference between revisions
| Line 9: | Line 9: | ||
== Third-party MDM providers == | == Third-party MDM providers == | ||
[[Resco Mobile CRM]] app can be managed by MDM providers, such as '''Microsoft Intune''' or ''' | [[Resco Mobile CRM]] app can be managed by MDM providers, such as '''Microsoft Intune''', '''Citrix Xen Mobile''' or '''Google Enterprise Distribution'''. Our App Store / Play Store app can be used for MDM distribution with limited support of security features (see the [[Mobile device management#Security|Security section]] below). More advanced MDM integration requires requesting a [[Custom mobile apps|custom mobile app]] with MDM integration. | ||
MDM admins can control which version of Resco app is installed on the managed devices, or even restrict certain features of our app. However, Resco apps require a [[Resco_mobile_apps#App_permissions|set of permissions]] for their function, too strict control can break the app. | MDM admins can control which version of Resco app is installed on the managed devices, or even restrict certain features of our app. However, Resco apps require a [[Resco_mobile_apps#App_permissions|set of permissions]] for their function, too strict control can break the app. | ||
| Line 27: | Line 27: | ||
For example, if you have a custom JavaScript solution that you have meticulously tested with a certain version of the app or a finetuned custom integration solution, you might decide to skip some releases so that you don't have to test everything anew. However, in order to be eligible for Resco support, you need to update your app at least once a year. Also, the operating systems on mobile devices should be kept up to date at least once a year. | For example, if you have a custom JavaScript solution that you have meticulously tested with a certain version of the app or a finetuned custom integration solution, you might decide to skip some releases so that you don't have to test everything anew. However, in order to be eligible for Resco support, you need to update your app at least once a year. Also, the operating systems on mobile devices should be kept up to date at least once a year. | ||
If you want to use MDM for centralized distribution of the app on a larger number of devices, this should not be a problem. To this date, the Resco support team has been able to help with any requested MDM solution. In this scenario, the MDM provider should request a custom version of the Resco app, either as an IPA file (iOS) or APK/AAB file (Android). Resco support will provide a version of the app ready to be signed by the customer's provisioning profile and certificate. | If you want to use MDM for centralized distribution of the app on a larger number of devices, this should not be a problem. To this date, the Resco support team has been able to help with any requested MDM solution. In this scenario, the MDM provider should request a custom version of the Resco app, either as an IPA file (iOS) or APK/AAB file (Android). Resco support will provide a version of the app ready to be signed by the customer's provisioning profile and certificate. In the case of [[Custom mobile apps|Custom Mobile App]], you have full control over requesting the new version, and you’ll be served by our semi-automated build system. | ||
We have received reports from our customers, that in the case of iOS, many have successfully used the app store version of the app for distribution - no need for a custom installation file from Resco. However, we are happy to provide such custom files if needed. Contact Resco support for more information. | We have received reports from our customers, that in the case of iOS, many have successfully used the app store version of the app for distribution - no need for a custom installation file from Resco. However, we are happy to provide such custom files if needed. Contact Resco support for more information. | ||
| Line 34: | Line 34: | ||
In the case of security, the situation can be more complicated. The common use cases for security features of MDM include: | In the case of security, the situation can be more complicated. The common use cases for security features of MDM include: | ||
* Using key-value pairs for | * Using app-specific configuration (key-value pairs) for prefilling URL, name, etc. See [[Mobile_device_management#App-specific configuration support|App-specific configuration support section]]. | ||
* Setting up Exchange or SharePoint access | * Setting up Exchange or SharePoint access | ||
* Restricting the communication between the managed Resco app and non-managed apps | * Restricting the communication between the managed Resco app and non-managed apps | ||
* | * App-specific restrictions blocking features like copy/paste, taking screenshots, enforcing encryption, and much more | ||
* Initiating a private VPN to access protected enterprise resources | |||
* Enabling conditional access to enterprise resources | |||
{{Note|Keep in mind that if you block email clients, the app cannot send a log file to the support email address.|Warning}} | {{Note|Keep in mind that if you block email clients, the app cannot send a log file to the support email address.|Warning}} | ||
Enabling security features varies across different MDM providers and platforms. Some of them (e.g., Citrix on iOS or MS Intune on Android) require '''Mobile Application Management (MAM) SDK''' to be included in the app, while others (e.g., MS Intune on iOS) provide wrapping tools that take app installation (IPA / APK / AAB) and inject protection layer on a binary level. Some of the scenarios are described below. | |||
=== MDM support on iOS === | |||
iOS has support for MDM systems incorporated in the operating system. Some of the security features are supported out-of-the-box, even for apps having no specific MDM support. Here is the list of supported security features for specific MDM providers: | |||
{| class="wikitable sortable" | |||
! Feature || Microsoft Intune || Citrix Xen Mobile || Other MDMs | |||
|- | |||
| Deployment || AppStore app & custom apps || AppStore app & custom apps || AppStore app & custom apps | |||
|- | |||
| App-specific configuration || AppStore app & custom apps || AppStore app & custom apps || AppStore app & custom apps | |||
|- | |||
| App-specific restrictions || Custom app wrapped with Intune App Wrapping Tool || Custom app with Citrix MAM SDK || No support | |||
|- | |||
| Private VPN support and CA || Custom app wrapped with Intune App Wrapping Tool || Custom app with Citrix MAM SDK || No support | |||
|} | |||
=== MDM support on Android === | |||
Currently, we support only Microsoft Intune and Google Enterprise Distribution on Android. Google Enterprise Distribution is supported without any requirements for the app: even the Google Play store version can be used. Microsoft Intune support requires a custom-built mobile app with MS Intune MAM SDK opted in. | |||
Integrating the Android app with MDM is straightforward. You can typically choose the Play Store app from the list. In the case of custom mobile apps, choose the “Line-of-business app” option and upload the APK installation produced by our branding process. | |||
=== Use enterprise authentication on Windows apps === | === Use enterprise authentication on Windows apps === | ||
Revision as of 06:36, 28 September 2022
Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers and laptops.
Built-in features
Resco platform includes some traditional MDM features out of the box. The backend administrator can access the list of connected mobile devices, assign different security policies to users, remotely control/synchronize/wipe app from user device, and much more. See Enterprise security for more information.
Third-party MDM providers
Resco Mobile CRM app can be managed by MDM providers, such as Microsoft Intune, Citrix Xen Mobile or Google Enterprise Distribution. Our App Store / Play Store app can be used for MDM distribution with limited support of security features (see the Security section below). More advanced MDM integration requires requesting a custom mobile app with MDM integration.
MDM admins can control which version of Resco app is installed on the managed devices, or even restrict certain features of our app. However, Resco apps require a set of permissions for their function, too strict control can break the app.
MDM also adds another layer to the complexity of the update and change management. See best practices for upgrading Resco apps for more information.
Essentially, there are two main scenarios for MDM:
- Distribution
- Security
App distribution
The main motivators for centralized distribution are:
- manage the version that users have installed
- block access to the app store for security reasons
For example, if you have a custom JavaScript solution that you have meticulously tested with a certain version of the app or a finetuned custom integration solution, you might decide to skip some releases so that you don't have to test everything anew. However, in order to be eligible for Resco support, you need to update your app at least once a year. Also, the operating systems on mobile devices should be kept up to date at least once a year.
If you want to use MDM for centralized distribution of the app on a larger number of devices, this should not be a problem. To this date, the Resco support team has been able to help with any requested MDM solution. In this scenario, the MDM provider should request a custom version of the Resco app, either as an IPA file (iOS) or APK/AAB file (Android). Resco support will provide a version of the app ready to be signed by the customer's provisioning profile and certificate. In the case of Custom Mobile App, you have full control over requesting the new version, and you’ll be served by our semi-automated build system.
We have received reports from our customers, that in the case of iOS, many have successfully used the app store version of the app for distribution - no need for a custom installation file from Resco. However, we are happy to provide such custom files if needed. Contact Resco support for more information.
Security
In the case of security, the situation can be more complicated. The common use cases for security features of MDM include:
- Using app-specific configuration (key-value pairs) for prefilling URL, name, etc. See App-specific configuration support section.
- Setting up Exchange or SharePoint access
- Restricting the communication between the managed Resco app and non-managed apps
- App-specific restrictions blocking features like copy/paste, taking screenshots, enforcing encryption, and much more
- Initiating a private VPN to access protected enterprise resources
- Enabling conditional access to enterprise resources
| Warning | Keep in mind that if you block email clients, the app cannot send a log file to the support email address. |
Enabling security features varies across different MDM providers and platforms. Some of them (e.g., Citrix on iOS or MS Intune on Android) require Mobile Application Management (MAM) SDK to be included in the app, while others (e.g., MS Intune on iOS) provide wrapping tools that take app installation (IPA / APK / AAB) and inject protection layer on a binary level. Some of the scenarios are described below.
MDM support on iOS
iOS has support for MDM systems incorporated in the operating system. Some of the security features are supported out-of-the-box, even for apps having no specific MDM support. Here is the list of supported security features for specific MDM providers:
| Feature | Microsoft Intune | Citrix Xen Mobile | Other MDMs |
|---|---|---|---|
| Deployment | AppStore app & custom apps | AppStore app & custom apps | AppStore app & custom apps |
| App-specific configuration | AppStore app & custom apps | AppStore app & custom apps | AppStore app & custom apps |
| App-specific restrictions | Custom app wrapped with Intune App Wrapping Tool | Custom app with Citrix MAM SDK | No support |
| Private VPN support and CA | Custom app wrapped with Intune App Wrapping Tool | Custom app with Citrix MAM SDK | No support |
MDM support on Android
Currently, we support only Microsoft Intune and Google Enterprise Distribution on Android. Google Enterprise Distribution is supported without any requirements for the app: even the Google Play store version can be used. Microsoft Intune support requires a custom-built mobile app with MS Intune MAM SDK opted in.
Integrating the Android app with MDM is straightforward. You can typically choose the Play Store app from the list. In the case of custom mobile apps, choose the “Line-of-business app” option and upload the APK installation produced by our branding process.
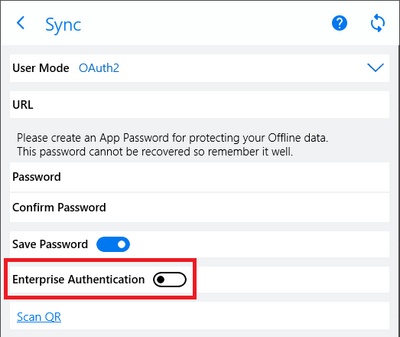
Use enterprise authentication on Windows apps
If you want to use authentication methods like conditional access, user certificates, or reverse proxy on Windows Desktop and Windows Store (UWP) apps, the mobile user needs to enable the Enterprise Authentication switch in the Sync window.
This option delegates the OAuth2 authentication flow to the default browser (which must be managed) and gets the authentication result back to the application using the app's URL scheme. Users might experience a confirmation dialog after successful login and they must confirm redirection to our app to deliver the result back to the synchronization dialog.
Remote Application Management tools
To simplify the initial user access to the Resco app, use push applications via Remote Device Management. Follow the below mentioned parameters in your MDM to have control over your enterprise mobility.
| Note | This is the Apple-defined protocol, therefore, it applies only to iOS users for all MDM providers. Since iOS version 9.3, the mobile application supports MDM key-value pair provisioning on iOS devices. |
You are able to specify the following parameters in your MDM:
| UserMode | (0:Standard, 1:External, 2: Anonymous, 3:CurrentWinUser, 4: OAuth2) |
| OrganizationUrl | |
| UserName | |
| Password | |
| Domain | |
| HomeRealm | |
| ADFSUsername | |
| SavePassword | (true/false) |
| ExchangeUrl |
| ExchangeEmail |
| ExchangeUserName |
| ExchangePassword |
| SharePointServerType | (0: SameAsCrm, 1: AD, 2: Online, 3: ADFS) |
| SharePointUserName | |
| SharePointPassword |
Once the above configuration is specified, the application skips the initial tutorial and shows the synchronization window (with the above values pre-filled) on the first run.