Connect Resco Cloud with Okta: Difference between revisions
Appearance
Marek Rodak (talk | contribs) No edit summary |
|||
| (7 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
{{ | {{Admin TOC}} {{Wikipedia|Okta, Inc.}} | ||
[[Resco Cloud]] supports Okta | [[Resco Cloud]] supports Okta authentication. | ||
== Prerequisites == | == Prerequisites == | ||
* To set up Okta | * To set up Okta authentication, you need Resco Cloud [[Releases/Summer_2022|version 15.1]] or higher. | ||
* To use Okta | * To use Okta authentication, the app also must be updated to [[Releases/Summer_2022|version 15.1]] or higher. | ||
== Okta configuration == | == Okta configuration == | ||
| Line 41: | Line 41: | ||
# In the Admin Console, go to '''Security > API'''. | # In the Admin Console, go to '''Security > API'''. | ||
# On the '''Authorization Servers''' tab, either modify the default authorization server or click '''Add Authorization Server''' to add a new one.<br>[[File:Okta add auth server.png|600px]] | # On the '''Authorization Servers''' tab, either modify the default authorization server or click '''Add Authorization Server''' to add a new one.<br>[[File:Okta add auth server.png|alt=Connect Resco Cloud with Okta: Configuration: Okta add auth server|600px]] | ||
#* As '''Name''', enter a name for authorization server, for example "resco cloud auth server". | #* As '''Name''', enter a name for authorization server, for example "resco cloud auth server". | ||
#* As '''Audience''', enter <code><nowiki>https://resco.net/rescocloud</nowiki></code>. | #* As '''Audience''', enter <code><nowiki>https://resco.net/rescocloud</nowiki></code>. | ||
| Line 57: | Line 57: | ||
#* Click '''Create'''. | #* Click '''Create'''. | ||
::[[File:Okta adding claims.png|600px]] | ::[[File:Okta adding claims.png|alt=Connect Resco Cloud with Okta: Configuration: Okta adding claims|600px]] | ||
== Connect Resco Cloud to | == Connect Resco Cloud to Okta == | ||
Resco Cloud | # Sign in to the Resco Cloud management console using a System Administrator user account. | ||
# Start the Resco Cloud [[Admin Console]]. | |||
# Select '''Settings > Organization''' from the menu to edit the properties of your organization. | |||
# In the '''Identity provider''' line, click '''Connect...''' | |||
# Select '''OKTA'''. | |||
# As '''Metadata URL''', enter the URL of your Okta authorization server (e.g., <code><nowiki>https://{your domain}/oauth2/default</nowiki></code>). | |||
# The read-only '''Redirect URI''' is provided for your reference (you need it for Okta configuration). | |||
# Enter the '''Client ID''' and '''Client Secret''' from Okta web app configuration. | |||
# Enter the '''Native Client ID''' from Okta native apps configuration. | |||
# Click '''Connect Now'''. | |||
# You are redirected to the Okta login page. Sign in and you return to the Admin Console with the Okta state set to '''Connected'''. | |||
== Assign Okta users == | |||
You have to assign Okta users to new or existing users of Resco Cloud. | |||
# In the [[Admin Console]], go to '''Resources > Users'''. | |||
# Select an existing user or create a new one. | |||
# As the '''Domain Name''', select the Okta login name (by default, this is the email address) of the user who you want to associate with the selected Resco Cloud user. | |||
In the | # Click '''Save & Close'''. | ||
As | |||
A red text saying '''Inactive''' is displayed next to the '''Domain Name''' until the user logs in for the first time. At that point, the text changes into a green '''Active'''. | |||
== Connect Resco mobile app to Resco Cloud that uses Okta == | |||
# Tap Synchronize. | |||
# As '''User Mode''' select '''OAuth'''. | |||
# Enter the URL of your organization, usually <code><nowiki>https://{organizationname}.rescocrm.com</nowiki></code>. | |||
# Enter a new password that protects your offline data (twice). This password cannot be recovered so remember it well. | |||
# Tap Synchronize. | |||
# Enter your Okta credentials. | |||
[[Category:Resco Cloud]] | [[Category:Resco Cloud]] | ||
Latest revision as of 09:36, 27 November 2023
| Resco Cloud administration |
|---|
|
|
Resco Cloud supports Okta authentication.
Prerequisites
- To set up Okta authentication, you need Resco Cloud version 15.1 or higher.
- To use Okta authentication, the app also must be updated to version 15.1 or higher.
Okta configuration
Log in to the Okta admin console as an administrator and set up app integrations for the web app and native apps, as well as an authorization server for Resco Cloud.
Web apps
- In the Admin Console, go to Applications > Applications.
- Click Create App Integration.
- As Sign-in method, select OIDC - OpenID Connect.
- As Application type, select Web Application.
- Click Next.
- Set up the new app integration:
- As App integration name, enter a name for your app integration, for example "resco cloud web app".
- As Grant type, select Refresh Token.
- As Sign-in redirect URIs, enter
https://<your_server_name>/Authenticate.aspx/ADFS. - As Sign-out redirect URIs, enter
https://<your_server_name>.
- Save all changes.
Native apps
- In the Admin Console, go to Applications > Applications.
- Click Create App Integration.
- As Sign-in method, select OIDC - OpenID Connect.
- As Application type, select Native Application.
- Click Next.
- Set up the new app integration:
- As App integration name, enter a name for your app integration, for example "resco cloud native apps".
- As Grant type, select Refresh Token.
- As Sign-in redirect URIs, enter
https://www.resco.net/oauth.html.
- Save all changes.
Authorization server
- In the Admin Console, go to Security > API.
- On the Authorization Servers tab, either modify the default authorization server or click Add Authorization Server to add a new one.
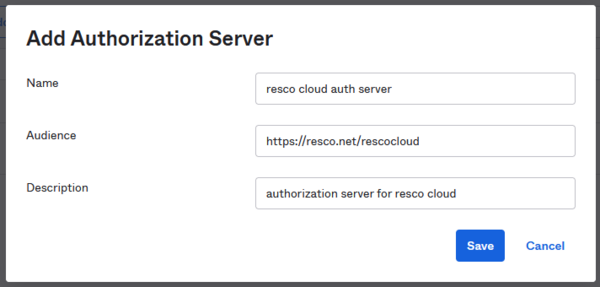
- As Name, enter a name for authorization server, for example "resco cloud auth server".
- As Audience, enter
https://resco.net/rescocloud.
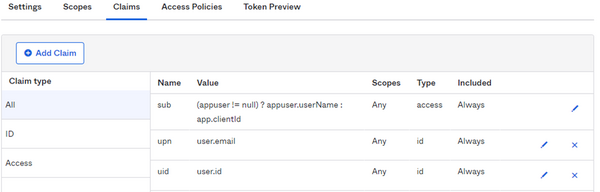
- Go to the Claims tab and click Add Claim:
- As Name, enter
upn. - As Include in token type, select "ID Token" and "Always".
- As Value type, select "Expression".
- As Value, enter
user.email. - Click Create.
- As Name, enter
- Add another claim:
- As Name, enter
uid. - As Include in token type, select "ID Token" and "Always".
- As Value type, select "Expression".
- As Value, enter
user.id. - Click Create.
- As Name, enter
Connect Resco Cloud to Okta
- Sign in to the Resco Cloud management console using a System Administrator user account.
- Start the Resco Cloud Admin Console.
- Select Settings > Organization from the menu to edit the properties of your organization.
- In the Identity provider line, click Connect...
- Select OKTA.
- As Metadata URL, enter the URL of your Okta authorization server (e.g.,
https://{your domain}/oauth2/default). - The read-only Redirect URI is provided for your reference (you need it for Okta configuration).
- Enter the Client ID and Client Secret from Okta web app configuration.
- Enter the Native Client ID from Okta native apps configuration.
- Click Connect Now.
- You are redirected to the Okta login page. Sign in and you return to the Admin Console with the Okta state set to Connected.
Assign Okta users
You have to assign Okta users to new or existing users of Resco Cloud.
- In the Admin Console, go to Resources > Users.
- Select an existing user or create a new one.
- As the Domain Name, select the Okta login name (by default, this is the email address) of the user who you want to associate with the selected Resco Cloud user.
- Click Save & Close.
A red text saying Inactive is displayed next to the Domain Name until the user logs in for the first time. At that point, the text changes into a green Active.
Connect Resco mobile app to Resco Cloud that uses Okta
- Tap Synchronize.
- As User Mode select OAuth.
- Enter the URL of your organization, usually
https://{organizationname}.rescocrm.com. - Enter a new password that protects your offline data (twice). This password cannot be recovered so remember it well.
- Tap Synchronize.
- Enter your Okta credentials.